

Be proactive about the security of your QuickBooks company file, and you’ll be less likely to encounter data theft.
Thanks to the internet, privacy has been on the wane over the last few years. We assume that our addresses and phone numbers are public information, thanks to sites like Switchboard and 411.com. We hope that our dates of birth are private (though the number of birthday wishes on Facebook makes that doubtful), and we assume that our Social Security numbers are hard to get.
Your customers trust you enough to provide you with additional private information, like credit card numbers. And you’ve seen what an uproar occurs when major corporate entities like Target and Home Depot get hacked.
Your small business may not have hundreds of thousands of customer information files, but you can still be targeted by external hackers and even your own employees. Are you taking measures to ensure the security of that data stored on your hard drive and/or in the cloud?
Your Inner Circle
The last thing you want to imagine is that one of your own employees has been tampering with your QuickBooks company data. It happens, though, and you need to protect yourself from potential internal attacks.
One of your internal controls, then, should include the establishment of boundaries for every employee who has access to QuickBooks. You can restrict each staff member to specific areas of the program instead of sharing a master password and giving everyone free rein. Go to Company | Set Up Users and Passwords | Set Up Users to do this.
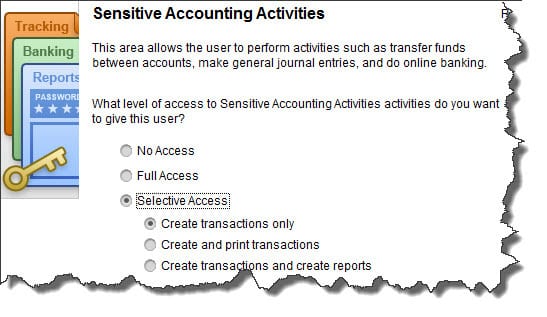
Figure 1: If you click on Selective Access in this window, you can restrict your employees’ activities to specific areas and actions.
The User List window opens, which will display all users who have been set up already, including you as the Admin. Click Add User and enter a name and password. Click the box in front of Add this user to my QuickBooks license, then click Next. Click on the button in front of Selected areas of QuickBooks. Click Next.
The next 10 screens break QuickBooks down into separate activities and activity areas, like Sales and Accounts Receivable, Checking and Credit Cards, and Sensitive Accounting Activities. On each screen, click on the button in front of the correct option:
Other Internal Controls
QuickBooks’ Audit Trail is your friend. It records everything that is entered or changed in the software, by whom, and precisely when. To view it, open the Reports menu, then click on Accountant & Taxes, then Audit Trail. Like all QuickBooks reports, it can be customized to display the entries you need to see.
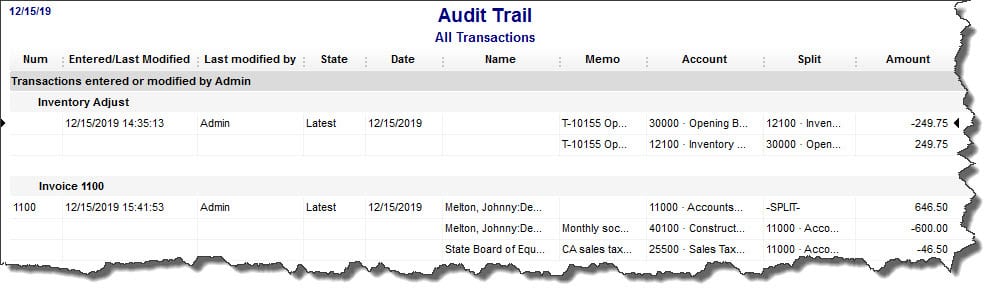
Figure 2: QuickBooks’ Audit Trail provides a detailed history of all activity in the software.
There are other reports that you should review frequently, and some that we should create and analyze for you at least every quarter, if not monthly. We can suggest reports that would help you look for fraud:
Common Sense Practices
When you run into problems with QuickBooks’ functioning, please let us help. Even a computer troubleshooting specialist will not understand the program well enough to solve problems, and he or she may compromise your data file further.
As security software and systems get smarter, so do the hackers. Don’t let your company and its customers be victims of data theft.
